Top 4 IT Utilities That EVERY Organization Should Be Using
- HTH

- Apr 15, 2021
- 3 min read
Every information security person knows that security is a state a mind as well as an implementation of defenses. With that, it is the job of the CISO (Chief Information Security Officer) to work on creating a secure minded business environment entirely and this should also be on the top of the priorities list for every organization's IT manager, regardless. With the effort to make every member of the workforce educated in security awareness the chances for attack can be reduced significantly. Here is a list of the top 4 utilities that every organization should be using in order to keep their company on the right side of due diligence security.
1. VirusTotal
VirusTotal is a website that will check to see if a file/website/hash or an IP address is malicious by testing it against numerous different antiviruses. This would be beneficial for employees to triple ensure that a file sent from another co-worker is safe and not harmful. Give it a try and see if any odd websites that you have visited have been flagged for malicious. https://www.virustotal.com/
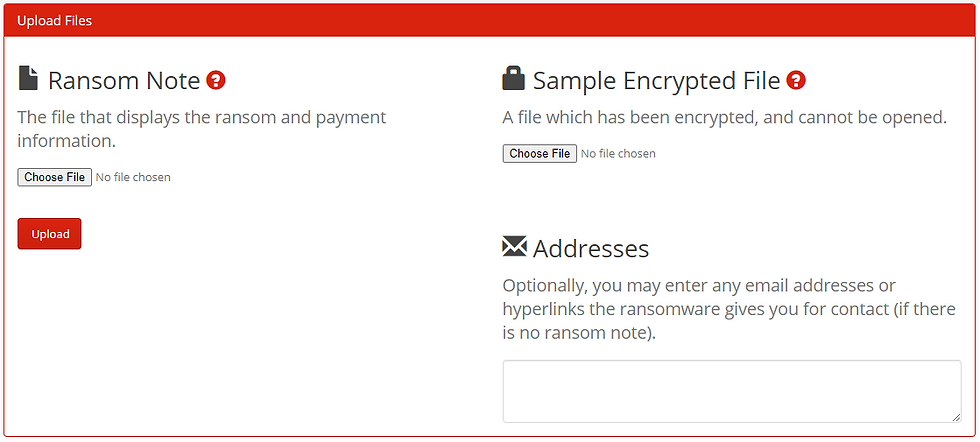
2. ID Ransomware
ID Ransomware is an amazing resource of a website that every organization should have bookmarked. If you or anyone you know has ever suffered from a ransomware attack that involves the lock/encryption of files then odds are that ID Ransomware may have been able to provide an encryption key for you. Well, potentially... ID Ransomware is a website that is comprised of a database of known ransomware encryption/decryption keys. So if you are hit with ransomware, with any luck it could be a common encryption algorithm and you could be a few click from getting your files back. https://id-ransomware.malwarehunterteam.com/
3. Bug Bounty

If your organization is need of additional security eyes to ensure vulnerability mitigation at a smaller cost then setting your business up with a bug bounty hunting program may be worth looking into. Bug bounty hunting is when hackers legally engage in finding security bugs inside of a company website or their network. Many websites (HackerOne, Bugcrowd, Intigriti) have become "middle man" platforms for security researchers and business organizations alike. Platforms like HackerOne allow professional ethical hackers and businesses to come together with a set of prewritten terms and agreements with defined target scopes and pay ranges. As a company you are even able to provide no rewards for bugs found and reported by security researchers although, this could have an effect of new-comers and beginner pentesters being the majority of researchers hunting for vulnerabilities for you. https://www.hackerone.com/ | https://bugcrowd.com/ | https://www.intigriti.com/
4. Have I Been Pwned
HaveIBeenPwned is a website where you can enter your email address to see if it has been logged in any known database breaches. This can be helpful in knowing if any employee work emails have been compromised inside of any databases along with the dates of compromise. Check it out and see if your email has been entered into any websites that have ever been hacked. HaveIBeenPwned also, does not add your email to a subscribers list when you check to see if you have been pwned. https://haveibeenpwned.com/
Utilizing these 4 IT utilities in your workforce environment will ensure a secure minded and safe practice amongst your entire organization and will further establish another wall of information security assurance.
Thank you for reading! If you enjoyed what you read be sure to check out the other articles.



_edited_edited.png)

.png)
.png)


.png)







Comments